Cyber security has become increasingly difficult to manage. Even when employees worked from one secure network, cyber was a challenge for many.
Now, we’re facing a reality where 67% of employees use personal mobile devices to access sensitive workplace data on the go, whether they’re supposed to or not. Worse, up to 51% of organisations globally have experienced data loss because those mobile devices weren’t secure.
Of course, that’s not to say BYOD wasn’t a saviour through 2020, but it’s vital to note that it also played a part in the 400% increase we saw during 2020. Still, 69% of IT decision-makers say BYOD is a good thing. The question is, how can you jump that security gap to start enjoying the benefits?
Ultimately, a mobile device management (MDM) security policy aims to do exactly this, but it’s a trend that’s not without issues. Done wrong, MDM can be confusing and costly. Hence why we’re going to simplify the process here, ensuring that you enjoy the benefits rather than potential pain points.
Suggested reading: To learn more about how to gain organisation support for your MDM policy, check out our free Board Presentation Template: Cyber Security and Threat Management Toolkit.
Understanding the Purpose of MDM
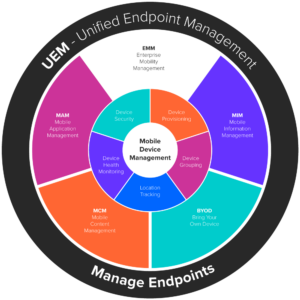
Until now, the majority of security focuses have centred around company data on in-house devices. But as we shift towards a remote working norm, these internal focuses simply don’t serve. Enter options like MDM. Using a list of approved devices, this endpoint security solution ensures that you know who’s accessing your network and what they’re doing once they get there. Implementation at any level can bring benefits including:
- Device provisioning
- Enrollment
- Device security
- Location tracking
- And more
Perhaps more pressingly this past year, MDM policies have proven important for making remote working possible in the first place. After all, remote teams need the ability to access operating systems and connect devices wherever they happen to be, a benefit that MDM makes possible while forever considering risks.
As mentioned, though, success here isn’t a given. Knowing what you need and how MDM can help you achieve that goal is fundamental to feeling these benefits. And, understanding the options available is often half of that battle.
Suggested reading: Has Remote Working Created a Massive Cyber Security Threat?
MDM vs MAM vs EMM
MDM is not the inclusive term we often consider it to be. In fact, standard policies can seem pretty outdated in the modern market, hence why MDM offshoots have come to the fore of late. Ultimately, the choices on offer each provide something different, and they include:
- MDM (mobile device management): MDM allows for the security of smartphones, tablets and other mobile devices used across companies. Devices can be locked, tracked, and monitored, with options for remote wiping, policies that restrict usage and enforcing virtual private network connections between mobile devices and enterprise servers.
- MAM (mobile application management): MAM is a more targeted solution that focuses on the control of applications and their data rather than data on the device itself. This allows for the containerisation of work and personal data, as well as restricting malicious apps and configuring or removing applications in keeping with company policy.
- EMM (Enterprise mobility management): EMM is an inclusive option that provides the benefits of both MDM and MAM solutions among others. EMM focuses both on devices connected and application management for inclusive mobile security across all remote working environments.
Pro tip: MDM solutions are undeniably valuable, but can be outdated and ill-equipped for 2021’s new normal. An inclusive EMM solution will secure your new working landscape more thoroughly, as well as growing with you, not against you.
Invest in a Technical Framework
Even an EMM policy will prove next to useless if you don’t consider its place within the wider framework of your company, specifically within your technical toolshed.
After all, EMM and MDM alike are not siloed solutions. Rather, they’re integrations that must fit into your existing technical infrastructure, and it’s down to you to make that possible. Fundamentally, you need to remember that MDM policies rely on endpoint software, or MDM agents, and also MDM servers based within either the cloud or a data centre. Those all-important policies are then pushed from that server to each applicable device, thus providing the security necessary. How achievable this is depends largely on finding the right solution for the right technology.
Pro tip: Take this opportunity to consider your software and whether it serves your increasingly remote needs. Changing your technology infrastructure once you’ve implemented an MDM policy will be expensive, disruptive, and a headache you most definitely don’t need in 2021.
Let’s say, for instance, that you rely heavily on the Microsoft umbrella across your workplace. An MDM that focuses on platforms like iOS simply wouldn’t offer the security you’re after. Rather, you need to seek an endpoint solution that can integrate with and oversee every application within Office 365, etc., such as Microsoft InTune. This cloud-based service focuses particularly on MDM within Microsoft suites, as well as bringing the notable benefit of integrating with Microsoft Defender. All of this leads to MDM policies with impact, cost-effective solutions, and easy implementation even while you’re all out of the office.
Perfect Your People Policy
People should also be at the heart of MDM (or EMM) implementation. Ultimately, letting your team know exactly what they can and can’t do where BYOD and general data usage is concerned should be a key priority to ensure you both adhere to data protections and know where branches originate if they do occur. But, before you can do that, you need a policy that knows the what, why, and how or your security focuses.
The Right MDM Policy for Your People
In some ways, this goes back to the whole MDM vs MAM vs EMM argument — the right type of coverage being key to letting your team understand what security is doing. But, a successful policy should go further, taking into account your risk profile and appetite, and making sure everybody understands those boundaries. Even if you think you’ve got these fundamentals sorted, the changing nature of security, specifically from outside devices, means that it’s always worth seeking a cyber security risk assessment ahead of any major implementations. Then, setting a policy people can understand comes down to:
- Considering device deployment;
- Understanding who needs access to what;
- Determining what each employee can do within company networks;
- Clear procedures for the event of device loss/theft.
Pro tip: Always seek software that allows you to set permissions and limit access as necessary. That way you can rest easy, and your team will forever know where they stand.
MDM, Endpoint and MDR
MDM, EMM and more are all important, but none are an island. Ultimately, a siloed approach is going to hinder rather than help BYOD efforts. In some ways, this is where EMM comes in, and tech like InTune will also help you get security off the ground. Ultimately, though, you need something that will take the work out of MDM.
MDR (Managed Detection and Response) and endpoint security technology (like Microsoft Defender for Endpoint) is a combination solution that we believe can significantly help businesses create a more flexible cyber security programme able to accommodate both BYOD and remote access.
With our endpoint focus that protects networks rather than devices (as any MDM policy should), our managed detection and response (MDR) service can take the pain out of MDM by focusing on the flexible policy frameworks modern workplaces need — providing rapid response to any threat that occurs and prevent an incident from becoming a breach. Our experts will be on-hand to provide you with a range of benefits including:
- 24/7 service
- Ongoing analysis
- An integrated security ecosystem
- Regular reviews/recommendations
To learn more read – What is MDR?
What’s more, we understand the importance of cyber security as a journey rather than a destination, meaning that we’ll forever be on hand to help you stay at the forefront of BYOD changes and more as they happen. What could be better for simplifying your policies in a world where nothing, especially not security, is simple anymore?
If you want to learn more, check out our Cyber Security and Compliance service, or get in touch and one of our experts can walk you through the details today.
Subscribe to the newsletter today
Related posts
Six Reasons Private Cloud is Still Relevant…
Rumours of private cloud’s demise have been greatly…
Changes to Microsoft Enterprise Agreements: Guiding You…
Some Microsoft customers are no longer able to…







